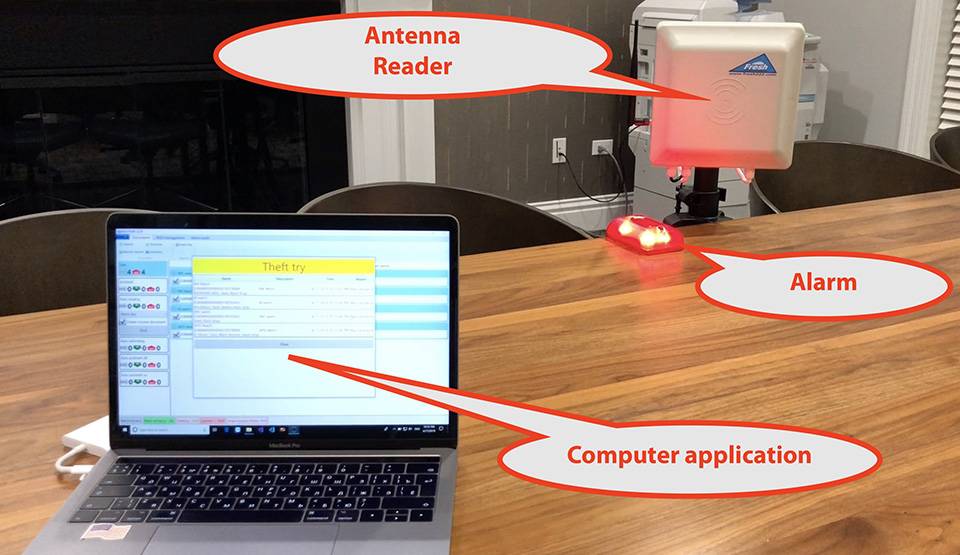
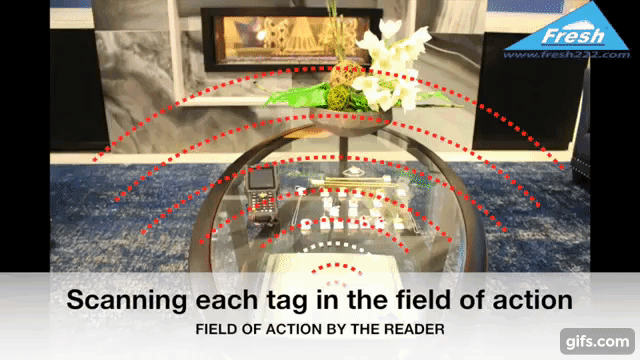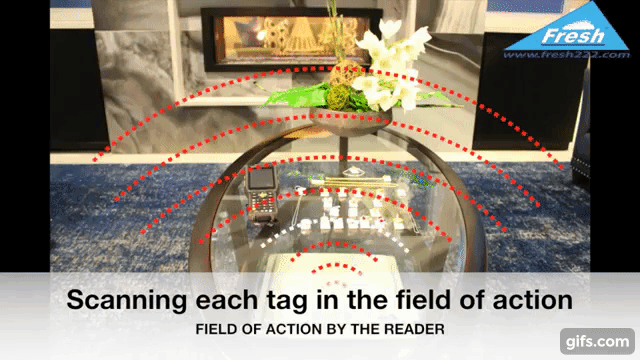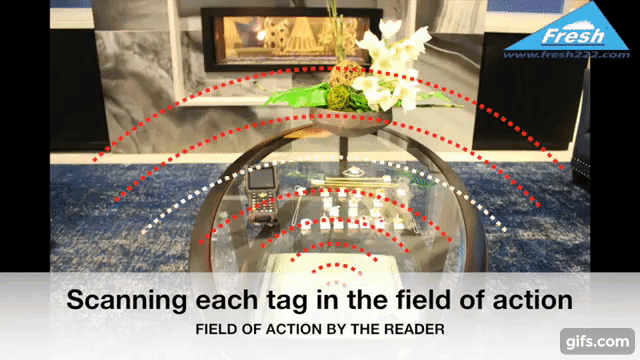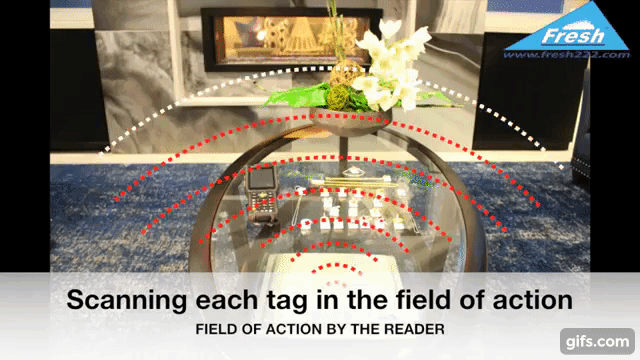
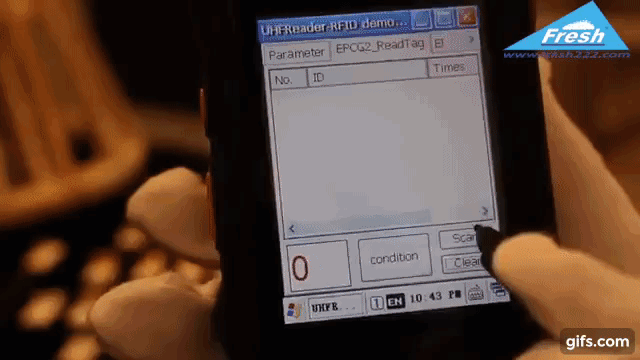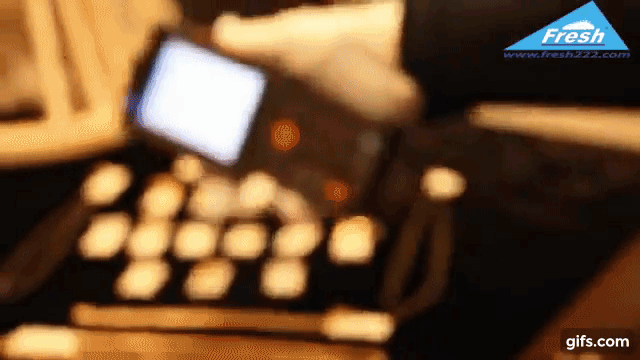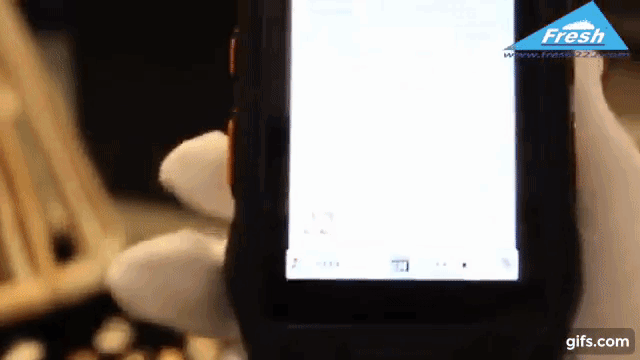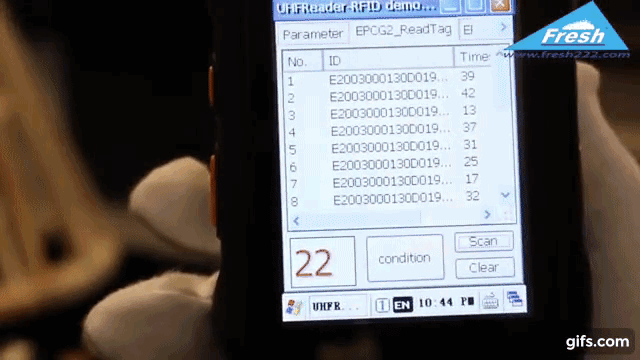
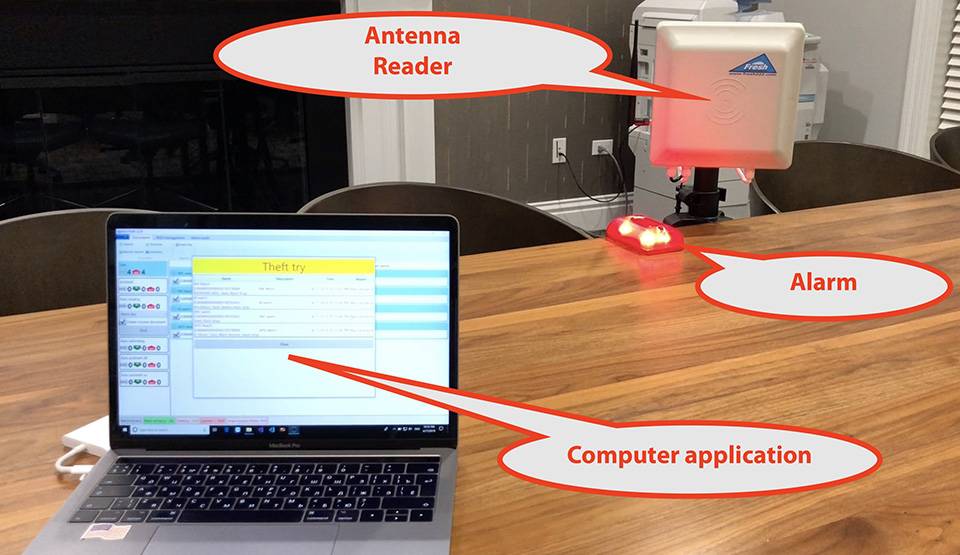
Radio Frequency Identification (RFID) technology uses electromagnetic fields to identify and track tags attached to objects. In the context of jewelry protection, specialized RFID tags are affixed discreetly to each piece. These tags store unique identifiers, allowing readers to detect, record, and monitor inventory in real time.
Conventional door alarms may only trigger once an item crosses a threshold. RFID, however, generates alerts when pieces disappear from the designated zone or when tags are tampered with. This proactive approach helps deter criminals before they can escape.
Standard systems often trigger false alarms when they detect generic magnetic or metal objects. By contrast, RFID precisely reads unique identifiers embedded in jewelry tags, minimizing nuisance alarms.
Manual audits of high-value items are time-consuming and prone to human error. RFID-based solutions allow near-instant inventory checks, ensuring that discrepancies are caught early.
Specialized RFID tags are sized to fit discreetly on rings, bracelets, watches, and other valuable items. These tags remain fully functional even when handled frequently by customers or staff.
Readers must be positioned to cover display cases, storage safes, and entry/exit points. In some setups, ceiling-mounted antennas or under-counter readers help maintain a clean aesthetic while still providing comprehensive coverage.
Seamless integration with on-site alarms provides an additional security layer. Whenever a tag goes beyond a preset distance, the system can automatically lock doors, alert security personnel, or trigger audible and visual alarms.
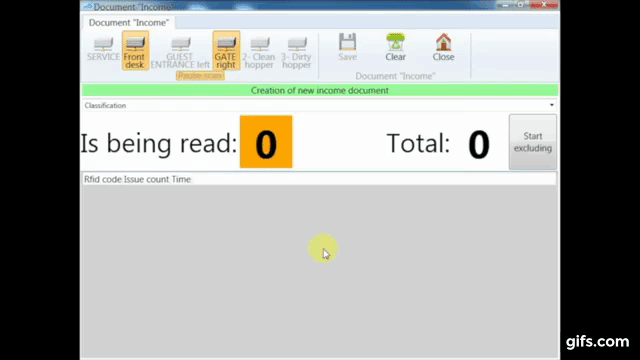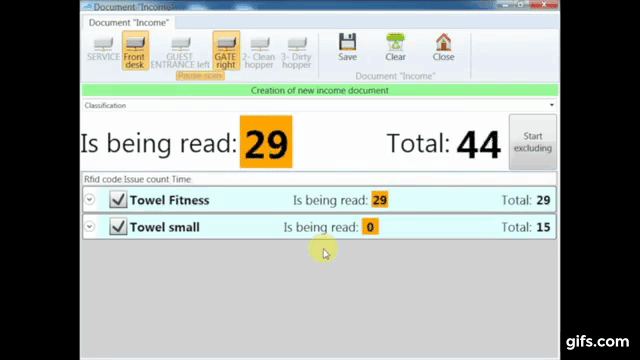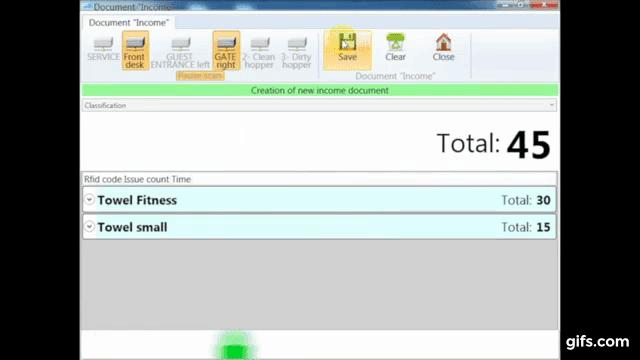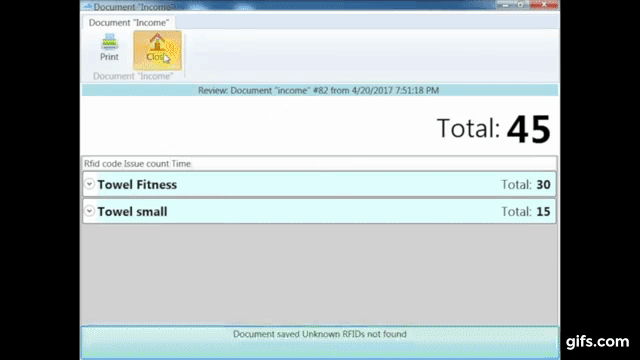
Smart shelves contain embedded readers and antennas that constantly scan tagged items. Once a piece is moved or removed improperly, the system instantly flags the anomaly. This technology helps maintain a free-flowing store layout while preserving maximum safety.
Real-Time Inventory Management
1. Automated Stock Updates
RFID enables automatic adjustments in the inventory database when a tagged item is purchased, returned, or moved to storage. This streamlined system reduces the possibility of miscounts and missing items.
2. Detailed Tracking and Analytics
Rich data collection allows managers to identify popular pieces, optimize product placement, and track movement trends. Detailed analytics also help store owners negotiate favorable insurance rates, as they can demonstrate proactive loss-prevention measures.
Optimizing Store Layout for Enhanced Protection
1. Strategic Display Arrangements
Valuable items can be placed in zones covered by multiple antennas, ensuring overlapping fields that heighten detection capabilities.
2. Creating Secure Checkout Areas
A designated checkout area can validate every purchase by scanning each item’s tag before removal, ensuring that only deactivated or approved tags leave the premises.
3. Concealed Infrastructure
Where aesthetics are paramount, readers can be discreetly installed behind wall panels, under counters, or within decorative elements. This helps preserve the store’s ambience without compromising security.
Training Staff to Maximize Security
1. Recognizing Suspicious Behavior
Team members should learn to monitor activities around high-value pieces. RFID systems are highly effective, yet human vigilance remains a critical layer of security.
2. Proper Handling of Tagged Items
Employees must be careful when displaying items to customers, ensuring they avoid damaging or removing tags. Should tampering occur, the system alerts authorized personnel.
3. Regular Process Audits
Periodic checks validate that both staff and equipment remain compliant with security protocols. Well-documented processes increase accountability and reinforce secure practices.
Comprehensive System Integration
1. Centralized Control Software
A single dashboard consolidates all event logs, sensor readings, and analytics, allowing for comprehensive oversight. Alerts, customer sales, and inventory movements are tracked in one place.
2. Third-Party Compatibility
Many RFID solutions integrate easily with advanced camera systems, door access controls, and temperature/humidity sensors. This unified approach empowers store owners to centralize risk management.
3. Offline and Cloud Backup
In instances of power loss or connectivity issues, having both local and cloud backups ensures that the latest data remains accessible and prevents disruptions in theft detection.
Future Innovations and Considerations
Emerging technologies like AI-driven analytics, integrated biometric scanners, and advanced motion detection are poised to enhance RFID’s capabilities even further. As the retail landscape evolves, RFID-based jewelry protection systems will likely merge with these innovations to deliver unparalleled accuracy in loss prevention, ensuring the highest level of safety and convenience for both retailers and clients.
Case Studies: Real-World Applications
1. Boutique Jewelry Store
We assisted a boutique jewelry store in integrating RFID tags on every high-value piece. The owners initially worried about the visual impact of tags, but after installing ultra-compact RFID labels and discreet antennas within the cabinetry, the store achieved near-complete theft prevention without compromising elegance. Our system’s continuous monitoring further helped them detect misplaced items swiftly, ensuring every piece was accounted for at closing time.
2. Luxury Watch Retailer
A high-end watch retailer needed a solution to reduce losses during busy periods. We implemented a combination of smart shelves and overhead readers. The result was a significant drop in suspicious activities, as alarms triggered whenever watches were removed from designated zones or obscured from reader view. By integrating these alerts with the store’s security cameras, staff could immediately identify individuals mishandling or attempting to conceal merchandise.
3. Department Store Jewelry Section
A major department store faced theft incidents in its fine jewelry section. Our RFID solution seamlessly integrated with existing point-of-sale systems, ensuring real-time updates whenever a sale was completed. The advanced reporting tools allowed management to review each day’s transactions and movement logs. Over time, they optimized product placement to reduce congestion around display areas—further enhancing both security and customer experience.
Calculating Return on Investment (ROI)
1. Reduced Shrinkage
RFID systems help eliminate expensive shrinkage issues by detecting theft attempts early. Stores often see a dramatic decrease in missing items, quickly offsetting the initial setup costs.
2. Labor Efficiency
Traditional inventory checks require considerable staff hours. By automating these tasks with RFID, employees can focus on customer service and sales, improving overall productivity.
3. Enhanced Customer Confidence
Visible evidence of stringent security measures can reassure customers that they are purchasing from a reputable retailer. This trust can lead to more sales, repeat visits, and positive word-of-mouth.
Implementation Roadmap
- Assessment and Planning
We begin by analyzing store layout, current security systems, and inventory management workflows. This assessment ensures correct antenna placement, tag selection, and software configuration.
- Pilot Deployment
We recommend installing the solution in one section to test performance, functionality, and staff training. This phase allows retailers to gather feedback and optimize the setup before a full rollout.
- Full Implementation
After successful pilot results, we integrate additional areas or entire stores. Our implementation team coordinates with store personnel to minimize disruptions to daily operations.
- Training and Support
Comprehensive staff training is essential. We provide guides, ongoing support, and refresher sessions to ensure continued proficiency and awareness of security protocols.
- Maintenance and Upgrades
Scheduled maintenance checks keep antennas and software in top condition. We also offer periodic upgrades to leverage new RFID developments, ensuring the system remains future-proof.
Maintenance and Best Practices
- Routine Equipment Checks
Verifying antenna, reader, and tag performance on a routine basis prevents unnoticed hardware malfunctions.
- Regular Tag Replacement
Although RFID tags are durable, certain retail environments may require periodic replacement of worn or damaged tags to maintain system accuracy.
- Software Updates
Upgrading security software introduces new features, bug fixes, and potentially stronger encryption. We ensure such updates occur seamlessly to minimize downtime.
- Audit and Reporting
Generating weekly or monthly reports helps identify patterns, detect anomalies, and confirm that staff and technology remain aligned with security goals.
Compliance and Insurance Benefits
1. Regulatory Requirements
Many regions require detailed documentation for high-value inventory. RFID’s automated logs and real-time tracking help meet or exceed these regulatory obligations.
2. Insurance Cost Reductions
Insurance providers are often willing to lower premiums for businesses that can demonstrate advanced theft prevention strategies. Our RFID system provides documented proof of a proactive loss-prevention approach.
3. Data Protection
Using secure communication protocols and encrypting sensitive information ensures compliance with privacy regulations. We help retailers protect not only their assets but also the integrity of customer data when necessary.
Employee Onboarding and Engagement
- Clear Guidelines We establish straightforward guidelines on how staff should handle tagged items, respond to alerts, and escalate potential theft scenarios.
- Role-Based Access Our software can be configured so that each employee level sees only the information relevant to their responsibilities, increasing efficiency and data security.
- Performance Incentives Management may choose to incentivize staff for strict compliance and vigilant monitoring, fostering a culture of shared responsibility for loss prevention.
Conclusion
RFID technology has radically transformed how businesses protect, track, and manage jewelry inventory. Our comprehensive approach—ranging from hardware deployment to staff training—empowers retailers to stay one step ahead of potential threats. By integrating cutting-edge RFID solutions with smart shelves, real-time analytics, and meticulous auditing, we offer a high level of security that instills confidence in both merchants and customers. Through consistent maintenance, upgrades, and staff engagement, businesses can maintain a sophisticated defense against ever-evolving theft strategies, ensuring their most precious assets remain secure.
FAQ
1. What is an RFID-based jewelry anti-theft system?
This system uses Radio Frequency Identification (RFID) technology to monitor and secure valuable items. Each piece of jewelry is tagged with a unique RFID chip, which is continuously scanned by readers placed in specific store areas. If a tagged item leaves its designated location or is tampered with, the system triggers an alert and updates the inventory records in real time.
2. How do RFID tags differ from traditional door security systems?
Unlike typical door alarms that only detect large metal or magnetic objects when they cross a threshold, RFID tags carry unique identifiers for each individual item. These tags can trigger alerts the moment a piece is moved or concealed, even before reaching an exit. This proactive detection helps deter theft and minimizes false alarms.
3. Are RFID tags visible to customers?
Jewelry RFID tags are designed to be discreet. They often take the form of tiny labels or embedded chips that do not distract from the item’s appearance. Many stores place them under clasps, hidden in watch straps, or behind decorative elements. These placement options ensure that customers can fully appreciate the piece without noticing the security mechanism.
4. Will the RFID system disrupt my store’s layout or ambiance?
Most RFID antennas and readers can be tucked away in smart shelves, under counters, or even above display cases. Readers can also be mounted on ceilings or within custom fixtures. This flexible placement strategy preserves the overall aesthetic while providing comprehensive coverage of the store’s valuable inventory.
5. Does the RFID system generate false alarms?
False alarms are rare with RFID because each tag has a specific identifier. The system only responds when it detects a mismatch—such as a tag leaving its assigned area, going out of range, or being tampered with. This precision dramatically reduces the nuisance of random triggers.
6. How often should tags or system components be replaced?
RFID tags are built to be durable, especially those designed for high-value goods like jewelry or watches. Most last for years under normal handling. Regular system maintenance ensures antennas, cables, and software remain in prime condition. Occasional checks help detect and replace any damaged tags.
7. Can this technology handle rapid inventory checks?
Yes. RFID readers can scan hundreds of tags within seconds. Some businesses use handheld RFID scanners to perform quick audits, ensuring the store’s inventory records match reality. This efficiency cuts down on manual counting and helps identify missing items much faster than traditional methods.
8. Does an RFID setup require specialized staff training?
Employees benefit from basic training to handle tagged items properly and respond to system alerts. However, RFID software is generally intuitive, and most tasks, including inventory updates, occur automatically in the background. A short training session is sufficient to get employees comfortable with the interface.
9. Will implementing RFID help with insurance claims?
Many insurance providers view RFID-based systems as a proactive loss prevention measure. By showcasing detailed records of how each item is tracked and secured, businesses may negotiate reduced insurance premiums. In the event of a claim, the system’s automated logs provide precise documentation.
10. How is data security maintained?
Modern RFID systems often use encrypted communication protocols to protect data transfers between tags, readers, and software. System administrators can assign role-based access to ensure that only authorized personnel can view or modify inventory records. Regular software updates also bolster cybersecurity.
11. Can RFID integration work alongside existing security measures?
Yes. RFID platforms are highly adaptable and can integrate with traditional alarms, CCTV cameras, motion detectors, and even environmental sensors. This unified approach offers a comprehensive security solution that covers physical, digital, and environmental risks all at once.
12. What is the typical return on investment (ROI)?
ROI varies by store size and theft rates. However, many businesses find that the reduction in shrinkage, faster inventory audits, and potential insurance benefits quickly offset the initial hardware and software costs. In addition, greater customer trust in a secure shopping environment can lead to increased sales and repeat business.
13. How do I get started with an RFID-based jewelry anti-theft system?
The process begins by consulting with an RFID specialist who can assess store layout, identify key risk areas, and recommend suitable tags and reader placements. From there, a pilot installation helps ensure the system meets operational needs. Once verified, the solution can be fully deployed across all relevant sections, followed by staff training and periodic maintenance.
By integrating a robust RFID solution, jewelry retailers safeguard their high-value assets, streamline their operations, and cultivate a trustworthy environment for shoppers. This technology ultimately empowers businesses to stay a step ahead of evolving theft tactics and maintain the highest standards of security.