Access control systems and software tailored for businesses of all sizes. FRESH USA offers ready-to-use, pre-programmed systems along with adaptable, customizable software solutions.
Access Control
Temperature Access Control, Product Details:
- Germany Heimann Infrared Sensor (Accurate temperature measurement, accuracy 0.2°C
- 2 million pixels dual camera
- 7 inch full view IPS LCD (flat style face recognition show)
- Shell waterproof
- RFID reader on request
Temperature Measurement New Trends in Smart Access Control
-
Uniqueness of Access Control
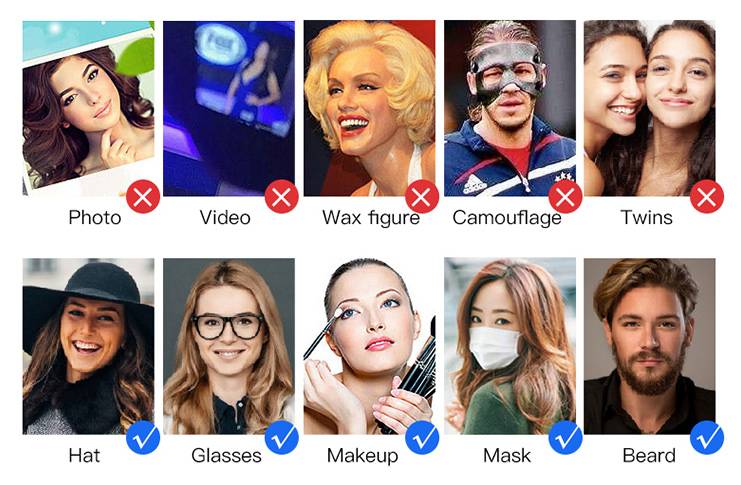
Face is unique, can not be copied, and prevent counterfeiting.
-
Non-contact temperature access control
No need to touch the equipment, it can be identified by entering the range, convenient for hygiene.
-
Convenience
No need to carry it, no need to cooperate, liberate hands, identify fast.
-
Safety
Never lost, not easy to copy, real people to prevent camouflage.
-
Stability
Different angles / different light / fade changes can be accurately identified.
-
Accuracy
Can quickly measure human body temperature and report unusual body temperature for unusual body temperature.
-
Concurrency
Simultaneous detection and identification of multiple faces, high recognition efficiency.
-
Easy to collect
No special equipment, mobile phone and computer camera can collect faces anytime anywhere.
The Drawbacks of Traditional Temperature Measurement
Non-contact temperature measurement safer
Our device has a built-in infrared non-contact / non-touch temperature measurement module.
When people are performing face recognition, it can measure their forehead and facial skin temperature at the same time. In a non-contact, accurate, reliable, efficient, and non-perceived way, the terminal will issue and unusual warning to those whose body temperature exceeds normal values, and show their temperature. At the same time, the temperature terminal may deny access. The built-in relay will block actuator.
Distance 30~50 cm Body temperature measurement
When people pass the control, face recognition can be performed. At the same time, the forehead and facial skin temperature can be measured. The temperature of the passing person can be quickly measured in a non-contact, accurate and reliable manner, and the unusual temperature can be detected and voice broadcast.
Support 1:1 And 1:N Identification
1:1 Brush documents to collect real-time portraits, compare the identity of the documents to judge the consistency of the person’s certificate, the accuracy rate is over 99%.
1:N Collect face information to build a face database, and quickly identify the face database with a hit rate of 99.99%.
HD Camera Real People Detection
Wide dynamic camera real people anti-counterfeiting, artificial intelligence deep learning function, intelligent recognition, eliminate camouflage – Secure.
Multiple Recognition Scenes Can Be Identified
The High-tech face recognition system prevents fraud.
200 W Pixel Camera
F1.6 super large aperture, wide dynamic image sensor, clear collection of every detail.
Blindness Algorithm
World-class face recognition algorithm-Blindness algorithm. Dynamic tracking detection based on video stream, with android quad-core system. Millisecond-level accurate recognition, the system runs more smoothly.
Automatic Fill Light
Infrared + RGB double fill light, easy to deatl with strong light, low light, night, backlight and other environments.
Large-capacity Face Database
30,000 face photos, 1 million identification records, 30,000 on-site snapshots
No fear of harsh enviroment
IP65 waterproof and dust proof, normal operation at 10~60ºC anti-glare, support outdoor open environment.
Support for External Multiple System
Construction site system
Access control system
Check-in system
Consumer system
Ticketing system
School management
Application
Suitable for construction sites, communities, schools, hight-speed rail stations, airports, hotel, government, offices, research, institutes, new retail, etc. UHF / HF RFID reader integration possible.
Package
Gallery
Get directions to Access Control by Fresh USA
Access Control Systems: Enhancing Security for Businesses of All Sizes
Introduction to Access Systems
In today’s fast-paced world, security is more important than ever. Access control systems are essential for managing who can enter specific areas within a building or facility. These systems not only restrict access to authorized individuals but also provide a way to track movements and prevent unauthorized entry. Whether you’re a small business or a large corporation, implementing an access control system can significantly enhance your security measures.
Types of Access Control Systems
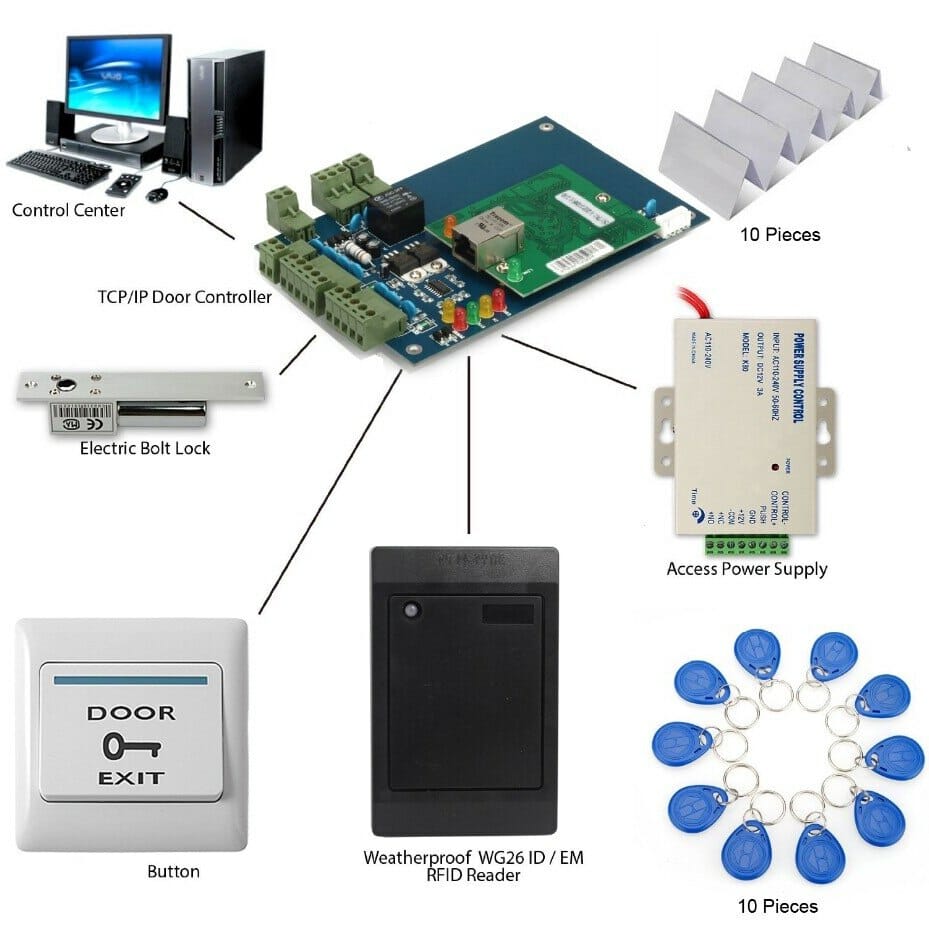
Key Card and RFID Long Range Readers
Key card and RFID long range readers are among the most popular access control solutions. These systems use embedded RFID microchips or proximity cards to grant access to authorized individuals. The long-range capability allows for seamless entry without physical contact, making it both convenient and efficient.
Proximity Readers

Proximity readers operate similarly to RFID systems but with a shorter range. Users simply need to bring their access cards close to the reader to gain entry. This type of system is commonly used in office buildings and residential complexes due to its reliability and ease of use.
Biometric Systems
Biometric access control systems use unique physical characteristics such as fingerprints, iris scans, or facial recognition to verify identity. These systems offer a high level of security as biometric traits are difficult to replicate or forge, making them ideal for high-security areas.
Keypad Systems
Keypad systems require users to enter a PIN or password to gain access. While they may offer less security compared to biometric systems, they are still effective for controlling access to less sensitive areas and provide a cost-effective solution.
Intercom Systems
Intercom systems utilize audio and/or video communication to verify the identity of visitors before granting access. They are particularly useful in residential buildings and offices where personal verification is necessary.
Integration with Other Security Measures

Access control systems can be seamlessly integrated with other security measures to create a comprehensive security solution. Common integrations include:
Video Surveillance
Combining access control with video surveillance allows for real-time monitoring and recording of access points, providing an additional layer of security and valuable evidence in case of incidents.
Intrusion Detection
Integrating access control with intrusion detection systems ensures that any unauthorized attempts to access restricted areas are immediately detected and addressed.
Alarm Systems
Alarm systems can be triggered by unauthorized access attempts, providing an additional layer of security and ensuring prompt response to potential threats.
Benefits of Access Control Systems
Enhanced Security
Access control systems significantly enhance security by restricting access to authorized individuals only. This reduces the risk of theft, vandalism, and unauthorized entry, making your premises safer.
Monitoring and Tracking
These systems allow for detailed monitoring and tracking of who enters and exits specific areas, providing valuable data for security audits and investigations.
Convenience and Efficiency
Access control systems streamline entry processes, reducing the need for manual checks and improving overall efficiency in managing access to buildings and facilities.
Challenges in Implementing Access Control Systems
Initial Costs
The initial cost of installing an access control system can be high, especially for advanced systems with biometric authentication and extensive integrations. However, the long-term benefits often outweigh these initial expenses.
Maintenance and Upkeep
Regular maintenance and updates are necessary to ensure the system remains effective and secure. This includes software updates, hardware checks, and troubleshooting, which can add to the overall cost.

Access Control Systems for Different Industries
Healthcare
In healthcare settings, access control systems protect sensitive patient data and restricted areas like pharmacies and operating rooms. They ensure that only authorized personnel can access these critical areas.
Hospitality
Hotels use access control to manage room entry and secure guest areas, ensuring a safe and comfortable environment for visitors. Key cards are often used to grant access to rooms and other facilities.
Corporate Offices
Access control systems in corporate offices protect valuable assets, confidential information, and ensure only authorized personnel can enter restricted areas. This is crucial for maintaining the integrity and security of sensitive business operations.
Parking Facilities
Access control systems manage vehicle entry and exit in parking facilities, enhancing security and streamlining operations. RFID systems are often used to allow quick and secure access for authorized vehicles.
Understanding RFID UHF Technology
Definition and Benefits
RFID UHF (Radio Frequency Identification Ultra High Frequency) technology is a sophisticated solution for access control. It uses electromagnetic fields to automatically identify and track tags attached to objects or individuals. The benefits include long-range detection, high-speed data transfer, and the ability to read multiple tags simultaneously.
Application in Modern Workplaces
RFID UHF technology is widely used in modern workplaces for managing access to secure areas, tracking inventory, and ensuring efficient operations. It is especially useful in environments where quick and hands-free access is essential.
Choosing the Right Access Control System
Factors to Consider
When choosing an access control system, consider the following factors:
- Security Needs: Assess the level of security required for different areas.
- Budget: Determine the budget for installation and maintenance.
- Scalability: Ensure the system can grow with your needs.
- Integration: Check compatibility with existing security measures.
Evaluating Security Needs
High-value assets such as servers and sensitive data require robust security measures like biometric systems. In contrast, areas like restrooms or common areas may only need basic keypad access.
Steps to Install an Access Control System
Initial Assessment
Start by assessing your security needs and identifying the areas that require access control. This will help in choosing the right system and equipment.
Choosing the Right Equipment
Select the appropriate access control devices based on your assessment, considering factors like security level, budget, and scalability.
Professional Installation
Hire professional installers to ensure the system is correctly set up and integrated with existing security measures. This ensures optimal performance and security.
Ongoing Maintenance
Schedule regular maintenance to keep the system functioning optimally and address any issues promptly. This includes software updates and hardware checks.
Future Trends in Access Control Systems
Cloud-Based Solutions
Cloud-based access control systems offer flexibility, scalability, and remote management capabilities, making them an increasingly popular choice for modern businesses.
Advanced Biometric Authentication
Future access control systems will leverage advanced biometric technologies, such as voice recognition and behavioral biometrics, for enhanced security and convenience.
AI and Machine Learning Integration
AI and machine learning will play a significant role in access control, enabling predictive analytics, automated threat detection, and more personalized security measures.
Case Studies: Successful Implementations
Example 1: Corporate Office
A leading Chicago-based corporation implemented a comprehensive access control system with biometric authentication and RFID readers, enhancing security and streamlining employee access.
Example 2: Healthcare Facility
A major healthcare facility in Chicago installed an access control system to protect sensitive areas and patient data, integrating it with their existing video surveillance and alarm systems.
Example 3: Parking Garage
A busy parking garage in downtown Chicago implemented an RFID-based access control system, improving vehicle flow and enhancing security for both vehicles and pedestrians.
Legal Considerations and Compliance
Data Privacy Laws
Ensure your access control system complies with data privacy laws, particularly when using biometric data, which is highly sensitive. Understanding these laws is crucial to avoid legal complications.
Compliance with Local Regulations
Familiarize yourself with local regulations regarding access control systems to ensure full compliance and avoid legal issues. This is important for both installation and ongoing operation.
Tips for Maintaining Your Access Control System
Regular Updates and Upgrades
Keep your system updated with the latest software and firmware upgrades to maintain security and functionality. Regular updates help protect against new security threats.
Routine Inspections
Conduct regular inspections of hardware components to identify and address any wear and tear or potential issues. This ensures the system remains reliable and secure.
Cost-Benefit Analysis of Access Control Systems
Long-Term Savings
While the initial costs may be high, access control systems offer long-term savings by reducing security breaches and operational inefficiencies. These systems can ultimately save money by preventing costly security incidents.
ROI Considerations
Consider the return on investment by evaluating the enhanced security, reduced risk, and improved efficiency provided by the system. A well-implemented access control system can offer substantial ROI through increased safety and operational efficiency.
Conclusion
Access control systems are indispensable for modern security infrastructure, especially in a dynamic city like Chicago. They offer enhanced security, efficient access management, and integration with other security measures, making them a valuable investment for businesses and organizations. By understanding the different types of systems, their benefits, and implementation challenges, you can make an informed decision to safeguard your premises effectively. By choosing Fresh USA, you are investing in state-of-the-art access control systems that prioritize security, efficiency, and adaptability. Elevate your security measures with Fresh USA‘s cutting-edge solutions today!
FAQs
What is the primary function of an access control system?
The primary function of a control system is to restrict and manage access to specific areas within a building, ensuring that only authorized individuals can enter.
How does biometric authentication work?
Biometric authentication works by verifying an individual’s unique physical characteristics, such as fingerprints, facial features, or iris patterns, to grant access.
Can access control systems be integrated with existing security systems?
Yes, control systems can be integrated with existing security systems like video surveillance, intrusion detection, and alarm systems to create a comprehensive security solution.
What are the common challenges faced during the installation of access control systems?
Common challenges include high initial costs, ensuring compatibility with existing infrastructure, and the need for ongoing maintenance and updates.
Are there cost-effective solutions for small businesses?
Yes, there are cost-effective access control solutions for small businesses, such as keypad systems and proximity readers, which offer reliable security without the high costs associated with advanced biometric systems.